A holistic and proactive approach to cybersecurity can help protect your industrial control system from hackers
In December 2015, 80,000 homes in the Ukraine were left without power when a cyber attack took down the electrical infrastructure. Investigations suggest that hackers used malware in conjunction with remote access to industrial control systems to directly interact with control systems, infect workstations and servers with malware, damage control-system hosts on workstations and servers, and block calls to customer call centers that would have alerted power companies to the outages.
A year prior, a German steel mill was the victim of a cyber attack. Investigations revealed that attackers used a spear phishing campaign — an email that appears to be from an individual or business known to the recipient, but isn’t. Instead, its from hackers who want financial, personal or login information found on that user’s PC. The attack was aimed at particular individuals in the company to trick them into opening malicious links. The opening of the links provided hackers with login information that granted them access to the plant’s network and control systems, resulting in failure of parts of the plant and the inability to properly shut down a blast furnace, causing “massive damage” to the equipment.
Clearly, as more industrial control systems connect to the Internet, they are becoming accessible to skilled hackers, resulting in an industrial landscape that is open to attack, an especially scary prospect for chemical processors.
How hackers gain access
“As we integrate more digitalization into our lives, we are increasing the attack surface available to hackers, says Andy Kling, director of cybersecurity and software practices with Schneider Electric (Andover, Mass.; www.schneider-electric.com). The use of tablets, smart phones and cloud storage is expanding at an exponential rate and, as a result, cyber attacks are more likely to avoid traditional security tools and infiltrate the workplace. Industrial targets aren’t necessarily secure on this fuzzy perimeter of our digital lives.”
As processors get smarter regarding cybersecurity, so too do hackers, who realize that the weakest link in the defense of industrial control systems is the humans who interact with them. “By tricking an employee into clicking on a link via a spear-phishing campaign, attackers can melt away defensive barriers, gain access to control systems and immediately take over the digital world of the plant,” warns Kling. “Once they do that, all bets are off.”
In addition, attackers can also enter a network via malicious links embedded in advertisements on websites where employees may browse, says Neil Peterson, director of DeltaV product marketing with Emerson Process Management (Austin, Tex.; www.emersonprocess.com). “Hackers can buy ad space on a reputable website and, embedded in that advertisement, can be malware. If an employee clicks the ad and your system is unpatched, hackers just injected malware onto your system and, from there, can begin to take control,” he says.
Another common point of entry is universal serial bus (USB) sticks. “People use them and aren’t aware that they contain malware. They plug [a USB stick] into their computer with the intention of moving data and accidentally infect the control system,” Peterson explains.
Adding to the complexity and severity of the situation, says Vincent Turmel, industrial cybersecurity consultant with Siemens Industry Services (Alpharetta, Ga.; www. siemens.com), is that it’s often difficult to patch or upgrade the equipment found on the operations side. “On the plant floor, PCs are used for a long period of time, so you often end up with a lot of older systems and various levels of legacy products that have different protection requirements and a range of patches and protections in place,” notes Turmel. “One of the greatest cybersecurity risks we encounter is trying to patch, maintain and defend the PCs on the plant floor. One size does not fit all when it comes to protecting PCs on the operations technology (OT) side.”
In addition, equipment used for operations is often tied into a larger system where, if you upgrade one part of the system, you have to upgrade all of it, which then becomes a cost issue, Turmel continues. “What this means is that even a common virus that’s been eradicated on the IT side, can wreak havoc on the OT side, due to the various ages of equipment and operating systems found on the plant floor.”
“Sometimes it feels like the only way to secure a computer after it has been connected to the network is to unplug it and throw it into a lake,” jokes Peterson. However, he is quick to add that cyber attacks on industrial facilities are no laughing matter as they may result in loss of assets and production dollars, theft of intellectual property or endanger the health and safety of employees and the environment.
Is the CPI at higher risk?
“We do see the risk for very specific attacks that can occur via PCs in today’s automation space,” agrees Anthony Baker, security leader with Rockwell Automation (Milwaukee, Wis.; www.rockwellautomation.com). Many of those attacks leverage known vulnerabilities in industrial control systems where owners of the systems have not been able to patch and maintain the systems used in their production space,” says Baker.
“When we talk to our customers about possible risks, we like to point out those concerning intellectual property because they are often not considered and are very applicable for the chemical industry in the form of recipes, process and information,” says Baker. “However, the more significant concerns are related to the risks associated with the integrity of their operations. If an attacker decides to tamper with operations or equipment, it may cause critical damage that jeopardizes production availability. But the most significant and frightening issues include attacks that would impact the safety of personnel, people in the vicinity or the environment.”
So, are the chemical process industries (CPI) at a greater risk for these types of targeted attacks than other industries? “While we can’t know for sure how likely there is to be an attack on any given plant or what type of attack it might be, we do know that there have been recent attacks on industrial control systems, so we know it’s possible to gain access to an industrial facility via the control system and cause damage,” notes Baker. We also know that attacks on a chemical facility have the potential to affect the broad population.”
For this reason, the U.S. Presidential Policy Directive on Critical Infrastructure Security and Resilience, which identified 16 critical infrastructure sectors in need of strengthening and protection, includes the chemical industry. “The chemical processing industry is listed as one — as a matter of fact it’s first on the list — of the critical sectors of this country and, as such, we have to consider that it is likely to be part of any cyber attack that might take place. If, how and where such an attack would occur would depend upon the motivation of the attacker, but some type of attack is obviously a real risk,” advises Schneider Electrics Kling.
How to protect your facility
“Today’s digital culture of bring your own devices, higher connectivity between the IT and the OT networks and remote and cloud connections can significantly increase the risk of a cyber incident on an industrial control system,” says Mike Baldi, chief cybersecurity architect with Honeywell Process Solutions (Houston, Tex.; www.honeywellprocess.com). “However, this risk can be managed by properly implementing new technologies on the industrial control system and integrating appropriate security controls with the new technologies.”
Determining the specific threats is the first step to deciding which of these technologies should be implemented, according to the experts. “Every facility — chemical and otherwise — has its own target-rich environment,” says Siemens’ Turmel. Figuring out your facility’s threat landscape includes trying to decipher who’s likely to break in and what their intent might be.
Turmel calls this threat-vectoring. “The first step in implementing a plan is to work with a cybersecurity service to determine the list of likely adversaries, how they would gain access and what they might be trying to accomplish,” he says. “From there, you conduct a vulnerability assessment and threat modeling, which becomes a guide to creating a holistic plan that considers and protects against specific threats to your facility so you are sure you are implementing the right tools. Then, when you have everything in place, you do threat-vectoring again and begin to test your defenses. You continue to add tools until you are as strong as you choose to be.”
The participation of industrial control-system suppliers, such as Siemens, in customer control system security continues to grow in importance. All industrial control-system owners should build a collaborative relationship with their supplier, including becoming familiar with the supplier’s cybersecurity organization. “The key to finding a security service provider is to find one that knows the plant-floor space, as well as cybersecurity,” notes Turmel. “They will coordinate activities, from assessments to implementation of managed services, to monitoring or patch management, to maintaining the infrastructure.”
“Assessments should also review policies and practices concerning Internet access to the control system and the use of industrial control-system protection for removable media, such as USB sticks, on every control workstation,” suggests Emersons Peterson.
Tools that assist with risk assessment are also available. “We have developed our Honeywell Industrial Cyber Security Risk Manager (Figure 1) specifically to address cybersecurity risk on industrial control systems,” says Baldi. “The product proactively monitors, measures and manages cybersecurity risk for industrial plants and systems. Through an interface, it allows users to prioritize and focus efforts on managing cybersecurity risks that are most important for reliable plant operations to provide an ongoing situation awareness of the cybersecurity posture of a control system.”

Figure 1. The Honeywell Industrial Cyber Security Risk Manager specifically proactively monitors, measures and manages cybersecurity risk for industrial plants and systems
Cybersecurity solutions
After the risk assessment, security tools should be implemented, but what types of solutions are being offered? “There’s a whole portfolio of cybersecurity solutions and technologies available to protect industrial control systems, ranging from end-point protection to network protection,” says Baldi. “The solutions portfolio includes both active and passive tools, tools based on known malware of cyber-attack signatures, tools that restrict the allowed operations and tools that are based upon cyber-attack behaviors.”
Traditional tools. Traditional, signature-based tools such as antivirus solutions, firewalls and deep packet inspection are still viable and advisable, but with the shear number of attacks and new viruses created each year, experts suggest that these alone are no longer enough to protect an industrial control system. “If all you have is a signature-based approach, eventually the software isn’t going to recognize a malicious signature and you’ll be exposed to a cyber attack,” says Kling. Instead, updated versions of these tools should be used in conjunction with other solutions to provide a holistic, proactive approach.
Whitelisting. Whitelisting, a newer signature-based solution, is currently being updated, improved and deployed for control systems, say the experts. Whitelisting is “superior to, but the opposite of antivirus technology,” says Emersons Peterson. “With antivirus tools, there are signatures that are discovered after viruses and malware become known. When antivirus software sees those signatures, the script is prevented from running. Whitelisting, however, assumes everything is bad, except the signatures the owner has deemed safe. This approach ensures that the file you are executing hasn’t been tampered with.”
In the past, he says, whitelisting required a lot of management because, if not properly deployed, it could prevent users from accessing their own system. However, Peterson says Emerson worked to improve and thoroughly test a new cybersecurity solution that includes whitelisting for its DeltaV control system that will provide high-level whitelisting protection without the high maintenance (Figure 2).
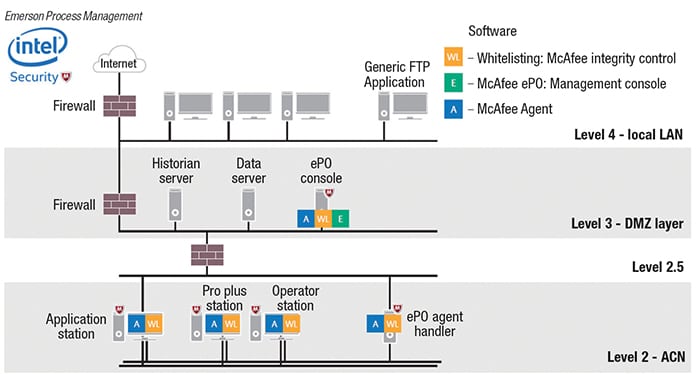
Figure 2. The DeltaV reference architecture includes the managed whitelisting protection based on the Intel Security Application Control for DeltaV workstations
Authentication. Authentication and authorization tools are also an important piece of the puzzle, according to Clark Case, security leader with Rockwell Automation. “Some control products, such as our FactoryTalk-enabled software products, provide user authentication and authorization, a method for access-control policies,” he says. Authentication and authorization technology provides secure access to the system, prevents unauthorized and unwanted changes from occurring in running processes or files and provides a documented audit trail of who made what changes and when.
Detect-and-respond. “Detect-and-respond” tools are another emerging solution. Rather than spotting malicious signatures, these solutions look for and recognize unusual behaviors taking place within the network (for example, excessive login attempts at the same workstation in a short window of time) and trigger an alarm. “This secondary class of tools is based upon artificial intelligence that has been available for years but is just now being applied to the security domain to recognize a pattern,” says Kling. “We believe the future of cyber defense lies in this type of tool.”
Experts now believe this type of visibility plays a big role in protection. So, a solution from cybersecurity start-up Indegy (Fort Worth, Tex.; www.indegy.com) monitors control-layer activity on PLCs via the network and on the actual controllers to detect cyber attacks before damage can occur. “Most solutions focus on protecting the management software, but attackers can compromise these platforms to hide the changes and status of the industrial process controllers so that everything appears normal, but this new approach monitors and provides visibility into the critical control layer of operational technology networks to identify threats in real time that place the safety, reliability and security of industrial control systems at risk,” says Dana Tamir, vice president of marketing with Indegy. The company’s solution comes in the form of a plug-and-play “box” that connects to a port on the network and, from there, provides monitoring and visibility of the controls and core technologies (Figure 3).

Figure 3. Indegy’s cybersecurity solution comes in the form of a plug-and-play “box” that connects to a port on the network and, from there, provides monitoring and visibility of the controls and core technologies
Protection from inside. A different approach, which protects from the inside out, comes from Bedrock Automation (San Jose, Calif.; www.bedrockautomation.com), which offers an industrial control system in which pins are replaced with an electromagnetic backplane, microcontrollers are secured with encrypted keys and TRNG is embedded in all system modules including the controller, power supply and I/O (Figure 4). All modules are encased in anti-tamper metal that is impenetrable without metal cutting tools and authentication extends throughout the supply chain, including third-party software and applications. “Cybersecurity ultimately comes down to protecting the computer,” says Albert Rooyakkers, founder, CTO and vice president of engineering, with Bedrock Automation. “You must solve the problem right at the submicron transistor level the same way you stop a viral contagion with a vaccine — from the inside out. So we’ve developed a cybersecurity solution where all the computing elements in the system are designed to be cyber hardened, from waking up with a secure boot to encryption keys that ensure that communications going in or out of the machine are authenticated. Traditional control systems have to wear armor to protect themselves, but we’ve built the protection right into the system,” he says.
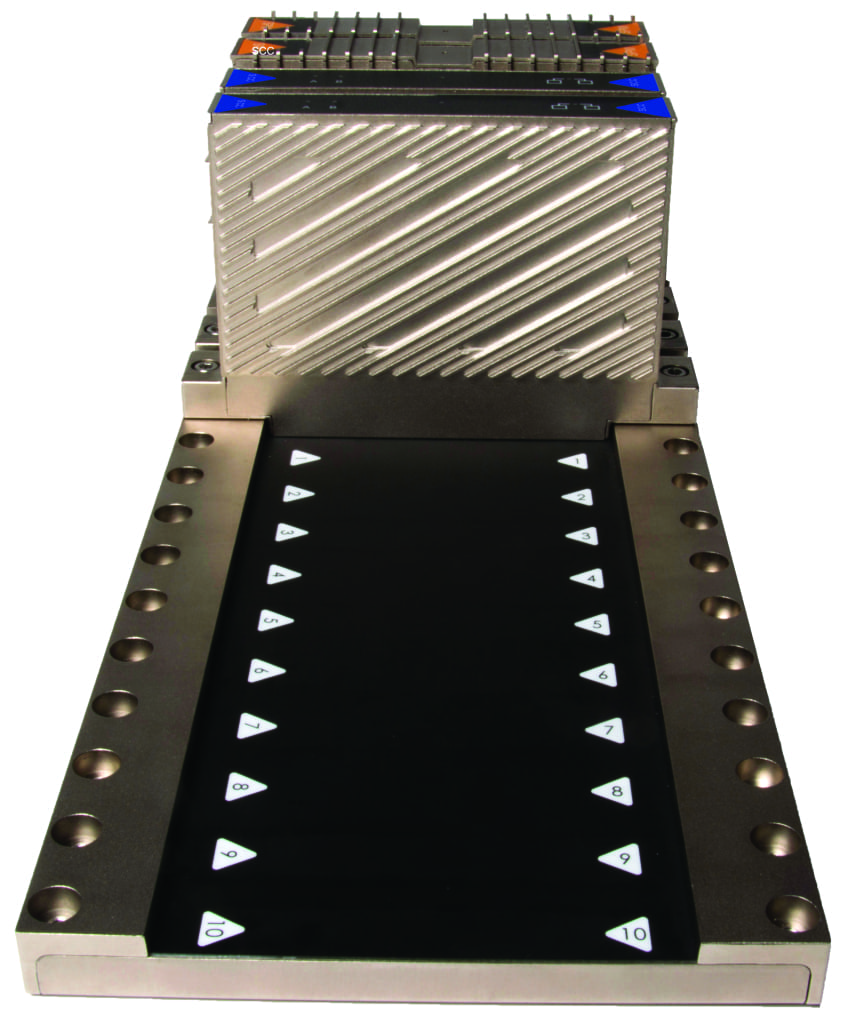
Figure 4. Bedrock Automation’s industrial control system replaces pins with an electromagnetic backplane (shown here), microcontrollers that are secured with encrypted keys and TRNG embedded in all system modules including the controller, power supply and I/O
An ongoing process
“When it comes to cybersecurity, the right solution won’t be a one-size-fits-all approach,” says Rockwell Automation’s Case. “The solution will depend upon the risk. Two facilities may have the same infrastructure but one produces distilled water and the other makes a dangerous chemical, so the required mitigations will vary greatly.”
The key is to fully understand the process, the risks and the vulnerabilities, and, based upon those, to identify the specific combination of solutions needed to create a holistic, proactive solution. But it doesn’t end there. Selected technologies must be installed and monitored and any internal, corporate cybersecurity policies needed to ensure proper use of the solutions must be enforced. However, since hackers never stop trying to find a way in, any protection must constantly be tested, updated and upgraded to thwart future methods of attack. Cybersecurity is not a one-and-done process. ■