It was clear at the recent Chemical Sector Security Summit (Baltimore, Md., July 31-Aug. 1) that awareness of and activity in security for the chemical process industries (CPI) are growing. The annual summit, now in its sixth year, was held at its largest venue ever and brought together about 650 participants from industry, academia and the government to network with other security professionals, share best practices and learn more about chemical security regulations.
One of the strong messages from this summit, as well as from additional sources, is that more attention than ever before is being given to cybersecurity of industrial control systems. In fact, in her introductory comments at the summit Suzanne Spaulding, deputy undersecretary for the National Programs and Protection Directorate (NPPD) for the U.S. Dept. of Homeland Security (DHS; Washington, D.C.; www.dhs.gov) emphasized an increased awareness of the interdependence between cyber and physical security and said that the “chemical sector has been a leader to bring together those two disciplines.”
Meanwhile, in his keynote address at the summit, undersecretary for the NPPD, Rand Beers, spoke of a new appreciation of owners and operators across all sectors, including the chemical sector, for the need for cybersecurity. He said that in the larger picture, security requires teamwork — across the government, private sector and the public.
That type of teamwork was evident in the mix of participants at the summit. Evidence is also seen in a number of working groups that are collaborative efforts to reduce the risks to industrial control systems. A good example of this is the Industrial Control Systems Joint Working Group (ICSJWG; www.us-cert.gov/control_systems/icsjwg/).
CFATS
The CPI are considered part of the critical infrastructure in the U.S., and as such are regulated by the DHS under the Chemical Facility Anti-Terrorism Standards (CFATS; for details on CFATS see Chemical Plant Security, Chem. Eng., pp. 21–23, September 2009).
While CFATS continues to be a driver for much of the heightened activity in security, the program itself has recently been confronted by serious challenges. Last year at this time, with strong support in both the House and the Senate, CFATS was poised to be reauthorized by Congress for multiple years (as opposed to the annual reauthorization it had been receiving). However, an internal assessment of the CFATS program in the last months of 2011 brought to light some serious concerns about the management and implementation of the program. A multi-year reauthorization now seems to be unlikely in the foreseeable future. While authorization inspections have resumed as of July 2012, the program is currently facing the possibility of drastic funding cuts.
During a “Congressional Perspectives” panel at the Security Summit, Monica Sanders, council for the House Committee on Homeland Security, shed some light on the CFATS situation. She explained that with a new program like CFATS, you want to have one-year authorizations until the program is “mature”, at which time it is extended for multiple years. “Congress thought that CFATS was at that point, but the late 2011 memo was a game changer”, she said, and heavy Congressional oversight is still needed on the CFATS program.
The panel members, which also included Chris Schepis, senior professional staff member for the House Committee on Homeland Security; and Jerry Couri, senior professional staff member for the House Committee on Energy and Commerce, seemed to agree that they expected CFATS would face a budget cut. The panel also commented, however, that Congress wants to see CFATS succeed as the kind of program envisioned in 2006 when it was first authorized.
While CFATS has been a driver for much of the heightened activity in security over the past few years, the goal of securing the CPI is not dependent on the standard. As Lawrence Sloan, president and CEO of the Society of Chemical Manufacturers & Affiliates (SOCMA; Washington, D.C.; www.socma.com) said in his opening remarks at the summit “… the reason we meet here is not merely because of the presence of a regulation, but because of a need for mutual collaboration… industry’s commitment to securing its most hazardous chemical products is stronger than ever, as evidenced by the overwhelming presence of so many attendees here today from the private sector. Others who are here who may not fall under CFATS or the Coast Guard’s MTSA [Maritime Transportation Security Act] program are also here to learn because, whether you are regulated or not, securing your assets and the communities in which you operate makes good business sense.”
Physical security
“Perimeter security is the first line of defense,” says Ryan Loughin, director of Petrochemical & Energy Solutions at Tyco Integrated Security (TycoIS; Boca Raton, Fla.; www.tycois.com), “and Tyco Integrated Security offers many solutions including advanced fiber-based technology, thermal imaging/infrared, analytics software and remote video products that help satisfy the CFATS Risk-Based Performance Standards”.
Indeed, most of CFATS addresses the critical need to physically secure chemical plants, with one of the major goals being to prevent theft and diversion. Diversion is a form of misappropriation, and refers to the acquisition of a material by means of deception, by someone who should not possess the material. While numerous forms of protection to avoid theft and diversion are employed at CPI sites, Tom Mann, CEO of TrakLok Corp. (Knoxville, Tenn.; www.traklok.com) sees a vulnerability during transportation. “Manufacturers of high-value and high-risk products have enormous security at their facilities,” says Mann, “However, when they ship product, they have had no other options than a padlock and a tracking device.”
Mann’s company, TrakLok, has introduced a new truck and container security device (Figure 1) that combines physical security with realtime global monitoring and notification. The lock integrates the physical security of a lock with a sophisticated system that monitors the security of cargo and instantaneously reports security breaches via cellular and satellite networks. TrakLok also offers a geofencing capability prohibiting the lock from opening if it is outside a prescribed area.
Cybersecurity
“Adversaries are becoming more stealth,” said Lisa Kaiser, operations lead, CyberSecurity Implementation, ICS-CERT, Office of Cybersecurity and Communications for the DHS, at the 2012 Chemical Sector Security Summit. In addition to the advanced complexity of threats, Kaiser said that there has been more than a 400% increase in the number of reported cyber-related incidents from 2010 to 2011. This statistic is from the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) Incidence Response Summary Report1, which shows that the number of reported and identified incidents impacting organizations that own and operate control systems associated with critical infrastructure rose from 41 in 2010 to 198 in 2011.
The threats. Kaiser cited an increased use of so-called spear-phishing involving major U.S. corporations including oil-and-gas, and water companies. Spear-phishing is a technique where malware-containing files are attached to very credible-looking emails, often seemingly from trusted sources. Clicking on the attachment unleashes the malware, which then opens the gates to the sender to access the computer system of the unsuspecting victim.
While most of the spear-phishing to date has been directed at information gathering, which in itself is reason to defend against it, the threat of being able to do more, such as take control of an industrial control system (ICS) is real and has been demonstrated.
Most users of ICSs are now aware of the Stuxnet worm, which was a real game changer for ICS security in that it was highly sophisticated and deliberately targeted to attack a control system (for more on Stuxnet, see Securing the CPI, Chem. Eng., pp. 17–20, September 2010; and Cybersecurity for Chemical Engineers, Chem. Eng., pp. 49–53, June 2011). New Stuxnet-like malware has since appeared, including Duqu, identified in October 2011 and Flame, identified more recently this year.
 |
Even if CPI control systems are not specifically targeted by this type of malware, “the fact that Stuxnet was wildly successful opens the door to collateral damage,” says Rick Kaun, business manager for the Industrial IT Solutions Group of Honeywell Process solutions (Phoenix, Ariz.; www.becybersecure.com). In addition to spear-phishing through social media like emails, Kaun says that the use of USB sticks and other devices with unknown content in work systems is also a big concern for ICS.
Andrew Ginter, director of Industrial Security at Waterfall Security Solutions (Calgary, Alberta, Canada; www.waterfall-security.com) echoes the concerns about collateral damage saying, “Thus far the intent [of the malware] is industrial espionage, but it is clear that they are capable of much more.” Industrial practitioners should not feel “secure” because they cannot point to a specific incident of harmful control, says Ginter. He explains further that if someone who shouldn’t have access to your control system does, that in itself is unacceptable. The ability for unauthorized remote control has been demonstrated and is a threat. Even without malicious intent, an uninformed hacker who has control can do damage.
Security experts. The suppliers of ICSs and security systems for them are continuously working on their arsenals to help prevent against cybersecurity threats.
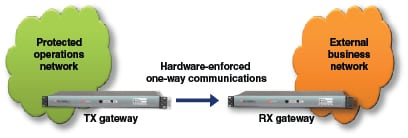
Waterfall’s Ginter says that one approach to address advanced threats is to use hardware-enforced one-directional communication (Figure 2) so that information can be shared out of the industrial control network to the business side, but no information can get back to the process control side. Oftentimes ICSs are connected to business networks to help track raw-material and product inventories, schedule maintenance and replacement part ordering and more. Advanced threats can, however, penetrate the firewalls that are used between the business and control systems. Unidirectional gateways are a hardware and software solution that permit the flow of information out of isolated networks, but not back into them.
Another tool that has been used in business IT environments but is relatively new to automation control systems is “whitelisting”. Honeywell’s Kaun explains that whitelisting means that “only predefined applications and processes are allowed on the ICS systems”. It protects from unwanted intrusions by allowing only those applications and files that have been placed on an approved list, and everything else is blocked. Anti-virus (AV) solutions on the other hand, are referred to as “blacklisting”, since they operate differently by blocking what is already known to be bad, but otherwise allowing everything else. Honeywell now offers a fully certified application and whitelisting solution to help combat malware from attacking its Experion Process Knowledge System.
“The end users of large companies are asking us to implement more security, including AV, whitelisting, firewalls etc.,” says Graham Speake, principal systems architect for Yokogawa Corp. of America’s (Newnan, Ga.; www.yokogawa.com/us) IA Global Strategic Technology Marketing Center in Dallas, Tex. “Some are also looking to have some or all of these services outsourced and managed by the vendor,” he says. Notifications of patches for various systems from various vendors can be confusing for end users to coordinate and implement correctly. Part of this, says Speake, is due to the fact that there has not been a definition of what to put into a “patch”. There is, however, an ISA99 (International Society of Automation; Research Triangle Park, N.C.; www.isa.org) working group that is addressing this need and preparing a draft standard for patch management in the ICS environment.
Speake says that Yokogawa offers users a field service where they will come in and implement upgrades and patches on a regular basis (quarterly, for example). While not yet widespread, this service is particularly useful for small-to-medium size companies who may not have the resources to keep their systems up-to-date. As security measures become more complex, more support will likely be needed.
No quick fixes. Security experts agree that the solutions to help thwart cybersecurity threats are not quick fixes. And, that while awareness of the vulnerabilities and threats is increasing, there is still a way to go. Looking forward, Yokogawa’s Speake says “the drive for products and devices that have security designed and built into them will become more intense. It is easier for vendors to build security in than for end users to add it on afterwards. It is the vendors’ responsibility to enable this security, and then the end user must take responsibility for keeping these products up-to-date and provide or outsource the services needed to monitor the security devices.”
“It [security] is a discipline much like safety and maintenance,” emphasizes Honeywell’s Kaun. The day he drives up to a plant and sees a sign that reads “So many days since a cybersecurity incident” next to the sign that says “So many days since a safety incident” is when he will feel that we have reached a good level of awareness.
Dorothy Lozowski
1. Available at www.us-cert.gov/control_systems/pdf/ICS-CERT_Incident_Response_Summary_Report_09_11.pdf
